Explore: Remote IoT Access Examples & Solutions
Is it possible to manage and control your devices from anywhere in the world? Absolutely, the advancements in remote IoT access have made this a seamless reality, transforming how we interact with technology and manage our lives.
First things first, let's clarify the fundamentals. RemoteIoT, specifically when coupled with SSH (Secure Shell) protocol, is all about using a secure method to connect to and manage your IoT devices from a distance. Consider it the digital key that unlocks remote control, enabling you to access and manipulate your devices, whether they're smart home gadgets or industrial-grade equipment.
Imagine the possibilities of managing a vast network of IoT sensors scattered across a remote location. Using SSH, you can connect to these sensors securely, retrieve the data you need, all without compromising the security of your system. This capability is no longer a futuristic concept; it's a practical solution, transforming the way we operate and interact with technology.
Let's dive into practical applications and the advantages it brings. Remote IoT device access isn't just a technological marvel; it's a powerful tool with a wide range of applications. Imagine being able to control your smart home from your phone, monitor industrial sensors from your office, or even troubleshoot a drone mid-flight. This is the essence of remote IoT device access.
RemoteIoT access examples highlight the versatility and power of IoT ecosystems, empowering users to streamline operations, boost efficiency, and slash expenses. Whether it's remotely fixing a smart thermostat or managing a fleet of industrial sensors, the applications are virtually unlimited. Homeowners can enjoy the convenience of remotely controlling devices like lighting, thermostats, and security systems. This boosts convenience and energy efficiency, all while providing peace of mind. RemoteIoT offers a strong platform that simplifies device management, guaranteeing seamless operations and enhanced security.
The use of remote access isn't likely to fade away. Instead, the technologies that enable it are constantly evolving. Users can, for instance, be granted access to control an HMI or patch an asset remotely. This continuous innovation guarantees that remote access remains a vital component of our interconnected world.
As technology continues to evolve, the demand for dependable remote access solutions will continue to rise. Take, for instance, medical equipment. Remote operation in the healthcare sector ensures that patients receive timely treatments. In factories, remote monitoring assists teams in managing machine performance and mitigating risks without a hitch. The possibilities are vast, and the benefits are clear.
Now, let's explore the ways remote access manifests in our everyday lives. An example of remote access is the ability to connect to another computer or network from a different location using a computer, smartphone, or tablet. There are several common scenarios where remote access comes into play. For example, if you need to access files on your work computer from home, you'll use remote access to do so. The ability to remotely access information and devices is a cornerstone of modern productivity and efficiency.
However, it's important to acknowledge the potential vulnerabilities. A 2023 report highlighted that a significant portion of cyberattacks exploit exposed Remote Desktop Protocol (RDP) services. This underscores the crucial need for secure remote access technology and robust security strategies.
Remote access security policies should be reviewed regularly, at least annually, or whenever there's a major change in the IT environment or a new threat emerges. This proactive approach helps safeguard your systems and data against potential risks.
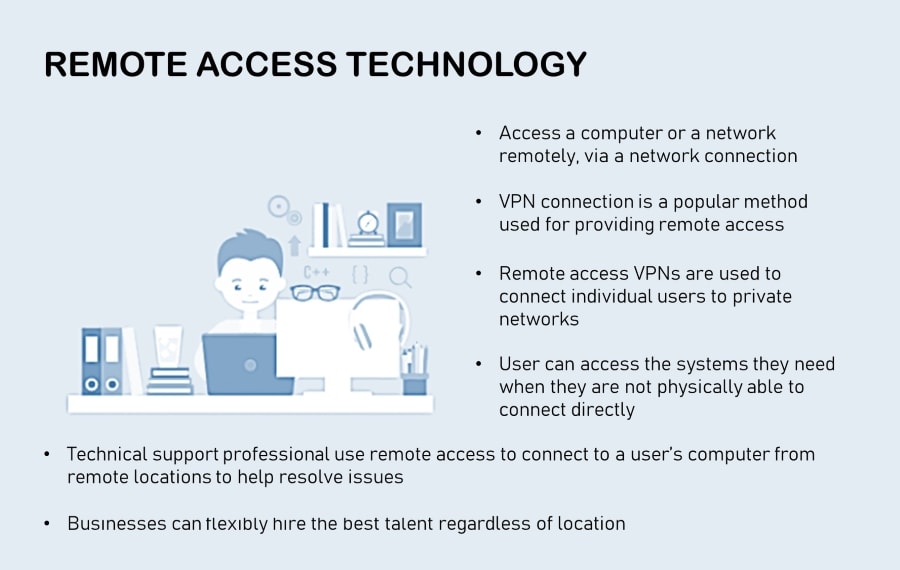
The benefits of remote access extend beyond convenience; it's a powerful tool for productivity. This process is facilitated by a remote access server, which allows for saved changes at another location and continued workflow and productivity away from the usual workspace. Whether you're connecting to a distant computer or network, the geographical location is no longer a barrier.
There are several industry-standard remote access software solutions available. For instance, Splashtop is a popular choice for business professionals and teams. This software is compatible with most computer operating systems and offers tailored plans based on business size and specific needs. Both unattended and attended access options are usually provided.
Remote access to IoT devices offers a multitude of advantages and conveniences that enhance our daily lives and provide valuable functionality. Lets break down some of the key reasons to access your IoT device remotely. Remote access allows you to control and monitor your IoT devices from anywhere in the world. Furthermore, with the rise of remote work, establishing secure remote access protocols is more critical than ever before.
Remote access solutions consist of tools or software used to give an authorized individual secure access to computers and devices from a geographical distance. These protocols control the connections between remote access servers and endpoints, allowing technicians to safely access endpoints from remote locations. This ensures secure, efficient, and reliable access to essential data and device functions.
The landscape of secure remote access has changed dramatically in recent years due to new technologies and circumstances, such as the pandemic. Remote access networks have also expanded their scope to encompass various forms of remote work and processes across locations. This expansion underscores the importance of secure and reliable remote access solutions.
With the use of remote network access, employees can work efficiently even when away from the office. Whenever you work with remote network access, one or more remote network access protocols come into play. These protocols are the backbone of remote access, ensuring secure and efficient connectivity. Remote IoT access examples in industrial settings include asset tracking systems, which use IoT sensors to monitor the location and condition of equipment and inventory.
Secure remote access incorporates a variety of security strategies designed to enable users to operate technology remotely while protecting the security of networks and data from unauthorized users. By permitting geographically dispersed access from a variety of devices, secure remote access supports business and IT operations while reducing the possibilities of a cyberattack.
Common examples of remote access technologies include remote desktop services, remote access software, and Virtual Private Networks (VPNs). These tools are essential for modern remote work and provide a secure, efficient means to access and manage data and devices from anywhere.
Understanding remote IoT access behind firewall examples is crucial for maintaining both security and accessibility. Firewalls play a critical role in protecting networks from unauthorized access. However, they can also hinder the seamless operation of IoT devices. Carefully configuring firewalls to allow secure remote access is essential.
Furthermore, the power of data analytics should not be overlooked. Use data analytics to gain insights and make necessary adjustments to optimize your system. By analyzing the data collected through remote IoT access, you can make informed decisions and improve the efficiency and performance of your devices.
Remote access tools allow people to connect, diagnose, and fix devices from anywhere. This capability is especially useful in fields like healthcare, where medical equipment can be operated remotely, ensuring timely patient care. In factories, remote monitoring helps teams manage machine performance and address risks without missing a beat. Whether its troubleshooting a smart thermostat or managing industrial sensors, the applications are virtually limitless.
In conclusion, Remote IoT access, particularly with SSH, is a powerful tool. It has revolutionized how we interact with technology, offering enhanced convenience, increased efficiency, and robust security. The examples and benefits are clear: whether it's controlling a smart home, monitoring industrial equipment, or troubleshooting devices from afar, remote access is here to stay, and its impact will only continue to grow.